Trusted at companies large and small
Highest security levels for peace of mind
Enterprise-grade security, governance, and monitoring is the backbone of Zapier's sophisticated, no-code platform.
No compromises on your data safety
Alongside our stringent internal security controls, we conduct annual SOC 2 (type II) audits.
Top choice for businesses worldwide
We're the automation platform of choice for 99% of the Forbes Cloud 100 companies and 69% of Fortune 1000 companies.
Industry standard compliance
Zapier is independently audited every year. Check out our 2022 SOC 3 report and request our SOC 2 report for more info.

Secure and safe data principles
In addition to using 256-bit AES encryption for safe data storage, Zapier also ensures secure network communication with TLS 1.2.
24/7 on-call security teams
Our globally distributed SRE and Security teams offer 24/7 availability. Plus, our status page provides real-time updates on our systems for all customers to see.
Comprehensive logging
Easily access Zap activity logs via your Zap History. That way, you can troubleshoot issues and verify information with just a few clicks.
Company-wide single sign-on (SSO)
Ensure secure access for your team using SAML 2.0 identity and access management (IAM) providers.
Account consolidation
See all existing and new Zapier users on your domain and consolidate them under your Company account.
User provisioning (SCIM)
Easily onboard and offboard team members through your identity and access management provider.
App restrictions
Limit which team members can integrate Zapier with sensitive apps, or block access to those apps completely.
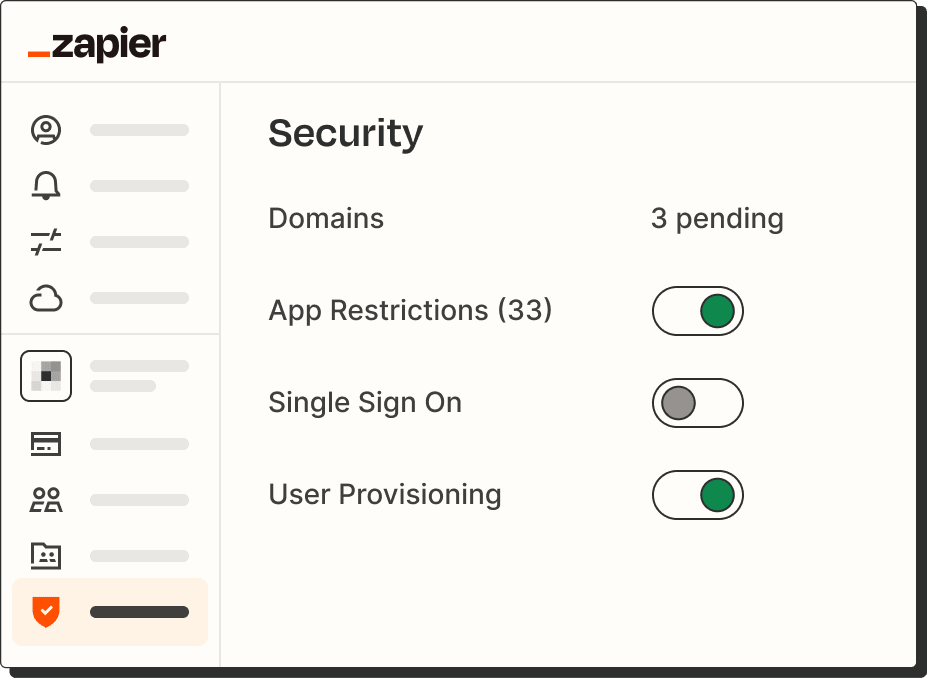
Advanced admin controls and permissions
By creating teams in your account, you can assign the same Zaps and app permissions to a select group of users. For example, you can only give specific teams or individuals access to apps or Zaps with customer information.
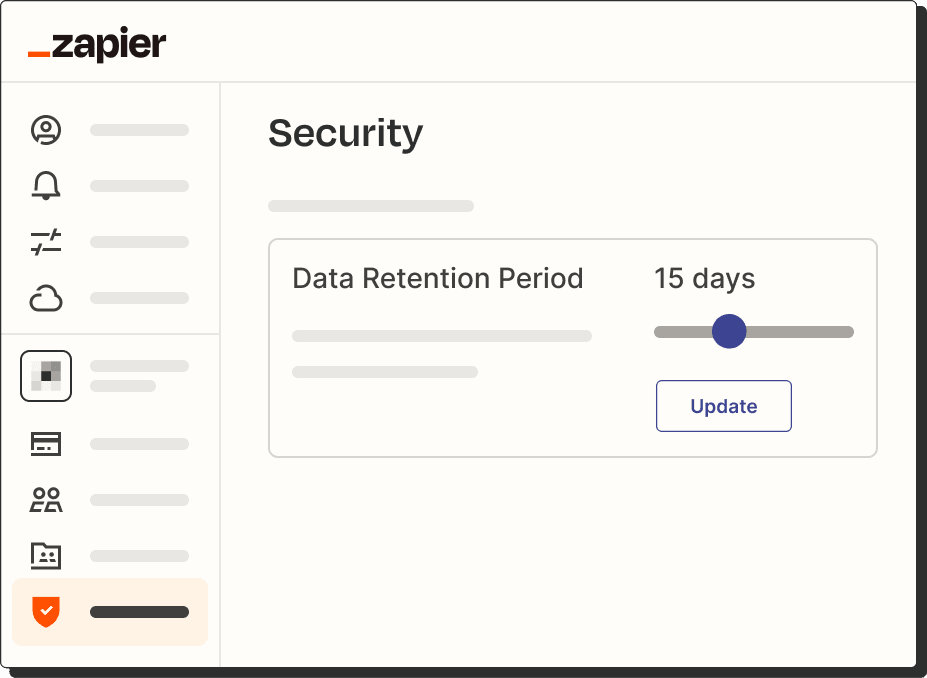
Custom data retention
Easily customize your data retention and deletion so you can meet your company's business, legal, or regulatory requirements.
Comprehensive security practices for businesses of all sizes
Product access control
Access to Zapier's customer data is restricted to authorized personnel based on your support requests and troubleshooting needs.
Change management
Every new Zapier feature or bug fix goes through peer review before publishing. We also perform regular static application security and robust unit testing.
Vulnerability management
We continuously scan for vulnerabilities and perform threat modeling exercises. Plus, we undergo a yearly external penetration test by an independent third party.
Cloud security
Zapier is hosted on Amazon Web Services (AWS) and leverages AWS's security and compliance controls for physical security and cloud infrastructure.
Security monitoring and logging
Zapier maintains both system and event-based security logs. These logs are centralized in a SIEM and monitored by our Detection and Response Team.
Bug bounty program
Zapier's security bug bounty program acknowledges and rewards the work of independent security researchers who identify and submit vulnerabilities.
Want to learn more?
Explore our security and compliance help documentation or contact Sales and get all your questions answered.
"At Outbrain, data security is a top priority, which means SAML authentication is absolutely essential. And we got it with our Zapier Company account."
Senior Online Acquisition Manager at Outbrain
"With Zapier doing the less creative work for us, we can actually focus on adding value through customer care rather than managing day-to-day operations."
GlobalCommunity Marketing Manager at Asana
